In today’s digital age, data has become one of the most valuable assets for businesses. From customer information to financial records, companies rely heavily on data to make informed decisions and drive growth. However, the increasing volume and complexity of data also pose significant challenges, particularly when it comes to storage and security. This is where secure cloud storage comes into play. In this article, we will explore the importance of secure cloud storage for businesses and how it can protect your valuable data.
The Importance Of Data Security
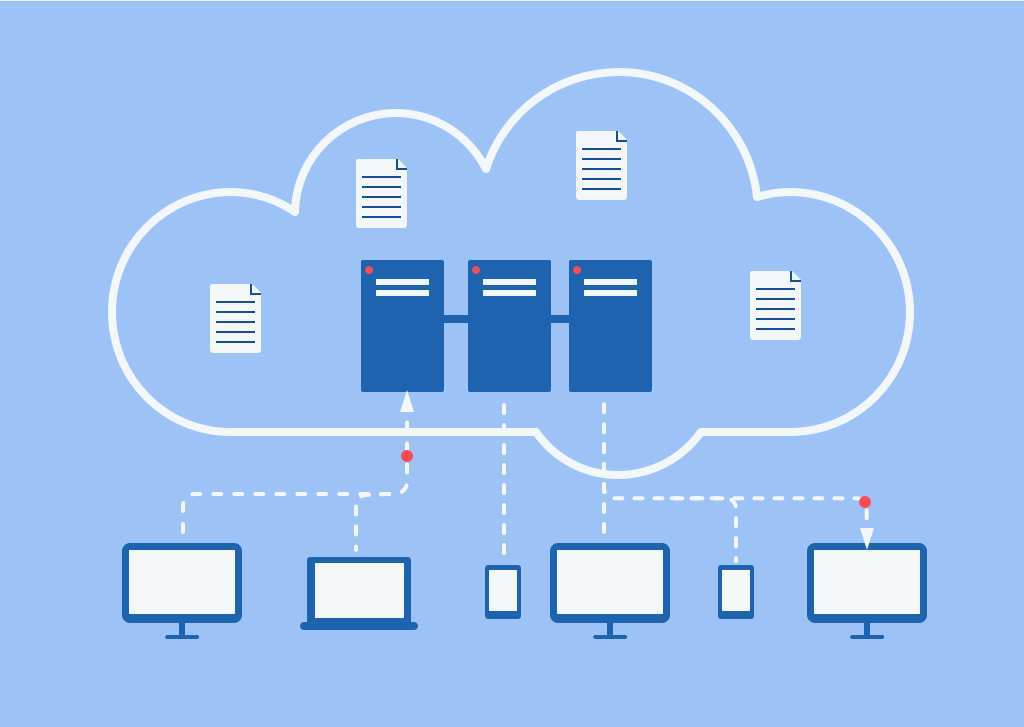
In an era where cyber threats are ever-present, safeguarding sensitive business data is of paramount importance. Traditional methods of storing data on physical servers or hard drives are vulnerable to theft, damage, or loss. Secure cloud storage offers a robust solution by storing data in remote servers with advanced security measures in place.
Understanding Cloud Storage
Cloud storage refers to the practice of storing data on remote servers accessed through the internet. It eliminates the need for physical storage devices and provides scalable storage options based on business needs. Secure cloud storage ensures that data remains accessible, protected, and available at any time and from anywhere with an internet connection.
Benefits Of Secure Cloud Storage
Secure cloud storage offers several key benefits for businesses:
- Enhanced Data Security.
- Scalability and Flexibility.
- Disaster Recovery and Business Continuity.
- Cost Savings.
- Collaborative Work Environment.
Enhanced Data Protection Measures
To ensure the security of your data in the cloud, reputable providers employ various protection measures:
- Encryption: Data is encrypted both during transmission and storage, making it unreadable to unauthorized parties.
- Access Controls: Multi-factor authentication and role-based access control systems limit access to authorized personnel.
- Redundancy and Backups: Multiple copies of data are stored across different servers to prevent data loss in case of hardware failures or disasters.
Choosing The Right Secure Cloud Storage Provider
When selecting a secure cloud storage provider, consider the following factors:
- Reputation and Reliability.
- Security Measures and Compliance.
- Scalability and Performance.
- Cost and Pricing Models.
- Customer Support and Service Level Agreements.
Best Practices For Secure Cloud Storage
Implementing best practices for secure cloud storage helps protect your data:
- Regularly update passwords and access credentials.
- Encrypt sensitive data before uploading it to the cloud.
- Monitor and audit user activity to detect any unauthorized access attempts.
- Train employees on cloud security practices and awareness.
Mitigating Risks And Ensuring Data Privacy
While secure cloud storage offers numerous benefits, it is essential to be aware of potential risks and take necessary precautions:
- Data Breaches and Cyber Attacks
- Vendor Lock-In
- Data Sovereignty and Jurisdictional Compliance
Compliance And Regulatory Considerations
Compliance with relevant regulations and standards is crucial when utilizing secure cloud storage for business. Depending on your industry and geographic location, certain regulations may apply, such as:
- General Data Protection Regulation (GDPR): If your business operates in the European Union or deals with EU citizens’ data, you must comply with GDPR regulations to ensure the privacy and security of personal data.
- Health Insurance Portability and Accountability Act (HIPAA): Healthcare organizations must adhere to HIPAA regulations to protect the privacy and security of patient health information.
- Payment Card Industry Data Security Standard (PCI DSS): If your business processes credit card payments, compliance with PCI DSS ensures the secure handling of cardholder data.
- Sarbanes-Oxley Act (SOX): Publicly traded companies in the United States must comply with SOX regulations to ensure the integrity and accuracy of financial data.
It is essential to work with a secure cloud storage provider that demonstrates compliance with relevant regulations and offers features and controls to help you meet your compliance requirements.
Cloud Storage Security Challenges
While secure cloud storage provides numerous benefits, businesses should be aware of potential security challenges:
- Data Breaches: Despite robust security measures, no system is entirely immune to data breaches. It is crucial to regularly monitor for any suspicious activities and promptly address security incidents.
- Data Loss: In rare cases, cloud storage providers may experience data loss due to unforeseen circumstances. Implementing regular backups and redundancy measures can mitigate the risk of data loss.
- Insider Threats: Unauthorized access by employees or insiders can compromise data security. Implement strong access controls and regularly review user permissions to minimize this risk.
Future Trends In Secure Cloud Storage
The field of secure cloud storage continues to evolve, with emerging trends that enhance data security and accessibility:
- -Zero-Knowledge Encryption: This encryption method ensures that only the data owner has access to the encryption keys, enhancing data privacy and security.
- Blockchain Technology: By leveraging blockchain, secure cloud storage providers can offer immutable and transparent data storage, reducing the risk of unauthorized data modification.
- Artificial Intelligence (AI) and Machine Learning (ML): These technologies can analyze patterns, detect anomalies, and improve threat detection and prevention in secure cloud storage environments.
Conclusion
In the digital age, secure cloud storage plays a vital role in protecting business data from unauthorized access, loss, and damage. By leveraging the benefits of secure cloud storage, such as enhanced data security, scalability, and cost savings, businesses can ensure the safety and availability of their valuable data.
Incorporating best practices, choosing the right provider, and addressing compliance considerations are essential steps in implementing secure cloud storage effectively. However, it is crucial to remain vigilant and proactive in mitigating risks and adapting to the ever-changing security landscape.