Cloud computing offers an array of benefits for businesses, but it also introduces potential security risks. Understanding and addressing these risks is essential to ensure the protection of sensitive data and maintain business continuity. This article delves into the security considerations that organizations should prioritize when adopting cloud computing solutions.
Understanding Cloud Computing
Cloud computing refers to the delivery of computing services over the internet. It allows users to access data, software, and applications on remote servers rather than relying solely on local infrastructure. While the cloud offers numerous advantages, it also presents unique security challenges that organizations must address.
Shared Responsibility Model
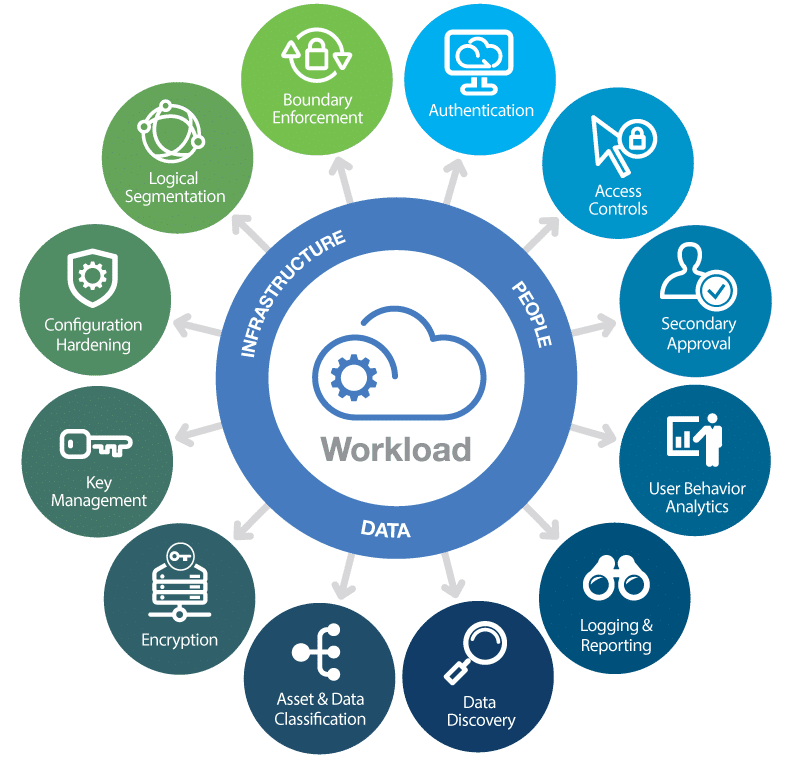
One important aspect of cloud security is the shared responsibility model. In this model, the cloud service provider (CSP) is responsible for securing the underlying infrastructure, while the customer is responsible for securing their data and applications within the cloud. It is crucial for organizations to understand their responsibilities and implement appropriate security measures accordingly.
Data Encryption And Privacy
Protecting data in transit and at rest is paramount in cloud computing. Encryption techniques should be employed to secure data as it travels between the user and the cloud service provider. Additionally, robust encryption mechanisms should be in place to safeguard data stored within the cloud. Privacy considerations, such as compliance with data protection regulations, must also be taken into account.
Identity And Access Management (IAM)
Implementing robust identity and access management practices is vital to ensure that only authorized individuals can access cloud resources. Strong authentication mechanisms, such as multi-factor authentication, should be implemented to prevent unauthorized access. Regular review and revocation of access privileges are also crucial to maintain the integrity of the cloud environment.
Network Security
Securing the network infrastructure is essential to protect cloud-based services. Firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs) are some of the security measures that should be implemented. Regular monitoring and auditing of network traffic can help detect and mitigate potential threats in a timely manner.
Vulnerability Management
Regular vulnerability assessments and penetration testing should be conducted to identify and remediate potential weaknesses in cloud systems. Patch management processes should be in place to address any vulnerabilities promptly. It is essential to stay updated with the latest security patches and updates provided by the cloud service provider.
Incident Response And Recovery
Having a well-defined incident response plan is crucial to effectively manage and mitigate security incidents in the cloud. Organizations should establish incident response teams, define escalation procedures, and conduct regular drills to ensure preparedness. Regular backups and disaster recovery plans should also be implemented to minimize downtime and data loss.
Compliance And Legal Considerations
Compliance with industry-specific regulations and legal requirements is essential when storing sensitive data in the cloud. Organizations should ensure that their cloud service provider complies with relevant security standards and regulations. They should also carefully review service-level agreements (SLAs) to understand the provider’s security practices and liabilities.
Training And Awareness
Employee training and awareness programs play a significant role in maintaining a secure cloud environment. Educating employees about best practices, potential risks, and the importance of security measures can help prevent inadvertent security breaches. Regular training sessions and awareness campaigns should be conducted to foster a security-conscious culture within the organization.
Third-Party Risk Management
When leveraging cloud services, organizations often rely on third-party vendors. It is crucial to assess the security posture of these vendors and evaluate their capabilities to protect sensitive data. Implementing robust third-party risk management practices, such as conducting due diligence assessments and monitoring vendor security, is essential to mitigate potential risks.
How To Ensure The Privacy Of Your Data In The Cloud
There are several important steps you can take. By implementing these measures, you can enhance the security of your sensitive information and maintain confidentiality. Here are some key practices to consider:
1. Strong Encryption: Encryption is a fundamental security measure for protecting data in the cloud. Before storing any data in the cloud, ensure that it is encrypted using robust encryption algorithms. This way, even if unauthorized individuals gain access to your data, they will be unable to decipher its contents without the encryption key.
2. Data Classification: Classify your data based on its sensitivity and importance. Categorize it into different levels, such as public, internal, and confidential. This classification will help you determine the appropriate security measures for each type of data. Confidential data should have stricter access controls and encryption compared to public data.
3. Access Controls: Implement strong access controls to limit who can access your data in the cloud. Use role-based access control (RBAC) to assign specific permissions and privileges to different users based on their roles and responsibilities. Regularly review and update access privileges to ensure that only authorized individuals have access to sensitive data.
4. Multi-Factor Authentication (MFA): Enable MFA for all user accounts accessing your cloud services. MFA adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password and a unique code sent to their mobile device. This reduces the risk of unauthorized access, even if passwords are compromised.
5. Data Loss Prevention (DLP): Implement a DLP solution to monitor and control the movement of sensitive data within the cloud environment. DLP tools can detect and prevent unauthorized data transfers, enforce encryption policies, and alert administrators about potential data breaches. This helps ensure that your data remains within authorized boundaries.
6. Regular Auditing and Monitoring: Set up comprehensive auditing and monitoring mechanisms to track activities and detect any suspicious or unauthorized access attempts. By regularly reviewing logs and monitoring user behavior, you can identify and respond to potential security incidents promptly.
7. **Contractual Agreements**: When selecting a cloud service provider, carefully review their contractual agreements, particularly the clauses related to data privacy and security. Ensure that the provider adheres to relevant regulations and industry best practices for data protection. You should also consider conducting a third-party security assessment to evaluate their security posture.
8. Data Residency: Understand the data residency and jurisdictional requirements for your organization. Some regulations may require that certain types of data remain within specific geographic regions. Ensure that your cloud service provider can comply with these requirements to maintain legal compliance and data privacy.
9. Regular Security Updates: Stay informed about the latest security updates and patches provided by your cloud service provider. Apply these updates promptly to protect against known vulnerabilities and security threats. Regularly check for any security advisories or notifications from the provider.
10. Employee Training and Awareness: Educate your employees about the importance of data privacy and security in the cloud. Provide training on best practices for handling sensitive data, recognizing phishing attempts, and using secure authentication methods. Regularly reinforce security awareness to promote a culture of data privacy within your organization.
By following these practices, you can significantly enhance the privacy and security of your data in the cloud. Remember that data privacy is an ongoing effort, and it is essential to regularly review and update your security measures as technology and threats evolve.
Factors To Consider When Choosing A Cloud Service Provider
There are several important factors to consider. The right provider will meet your specific needs and offer reliable services that align with your business goals. Here are key considerations to keep in mind:
1. Security Measures: Assess the provider’s security measures and protocols. Look for industry-standard security certifications, such as ISO 27001 or SOC 2, which demonstrate the provider’s commitment to maintaining a secure environment. Inquire about their data encryption practices, access controls, and incident response procedures.
2. Data Privacy and Compliance: Ensure that the provider adheres to relevant data privacy regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA). Verify their data handling practices, data residency options, and contractual commitments to protecting your data privacy.
3. Service Reliability and Uptime: Check the provider’s service level agreements (SLAs) to understand their uptime guarantees and downtime procedures. Look for a provider with a robust infrastructure and redundant systems to minimize the risk of service interruptions. Research their historical uptime performance and customer reviews for insights into their reliability.
4. Scalability and Flexibility: Consider your organization’s growth potential and ensure that the provider offers scalable solutions. Evaluate their ability to accommodate your changing needs, such as increased storage capacity or additional computing resources. Look for flexible pricing models that allow you to scale up or down as required.
5. Data Backup and Disaster Recovery: Inquire about the provider’s data backup and disaster recovery capabilities. Check if they offer automated backups, multiple data replication locations, and recovery time objectives (RTOs) that align with your business requirements. Understanding their disaster recovery plans and testing processes is crucial for minimizing data loss and downtime.
6. Technical Support and Customer Service: Assess the provider’s technical support options and response times. Look for 24/7 support availability and multiple channels of communication, such as phone, email, or live chat. Consider their reputation for customer service by reviewing testimonials or seeking recommendations from existing customers.
7. Cost and Pricing Structure: Understand the provider’s pricing structure and ensure it aligns with your budget. Evaluate the pricing models, such as pay-as-you-go or fixed-term contracts, and compare the costs of different service tiers or packages. Consider any additional fees for data transfer, storage overages, or support requests.
8. Service-Level Agreements (SLAs): Carefully review the SLAs provided by the cloud service provider. Pay attention to the performance guarantees, service credits, and dispute resolution mechanisms outlined in the agreements. Ensure that the SLAs cover critical aspects, including uptime, response times, and support availability.
9. Vendor Lock-In and Data Portability: Evaluate the ease of migrating your data and applications to another provider or bringing them back in-house if needed. Assess the interoperability of the provider’s services with other platforms and technologies to avoid vendor lock-in and enable flexibility in the future.
10. Provider Reputation and Financial Stability: Research the provider’s reputation within the industry. Look for reviews, case studies, and customer testimonials to gauge their track record. Consider their financial stability and long-term viability to ensure they will continue to invest in infrastructure and support.
11. Geographical Coverage and Latency: If your business operates in multiple regions, consider the provider’s data center locations and geographical coverage. Closer proximity to your target audience can reduce latency and improve performance. Ensure the provider has data centers in regions that comply with any specific data residency or regulatory requirements.
12. Cloud Ecosystem and Integration: Assess the provider’s ecosystem of services, APIs, and integration options. Check if they offer compatibility with the tools, platforms, and services your organization relies on. Consider the availability of third-party integrations and the ease of integrating with existing systems.
By considering these factors, you can make an informed decision when choosing a cloud service provider that aligns with your security, privacy, scalability, and business requirements. It is essential to thoroughly evaluate potential providers and select the one that best suits your organization’s needs.
Conclusion
As organizations increasingly adopt cloud computing, it is essential to prioritize security considerations to safeguard data and ensure business continuity. By implementing encryption and privacy measures, robust identity and access management, network security controls, vulnerability management practices, and comprehensive incident response plans, organizations can enhance their cloud security posture. Additionally, complying with legal and regulatory requirements, investing in employee training and awareness, and effectively managing third-party risks contribute to a robust cloud security framework.